Authenticating
Note: An OAuth server is currently in development and will replace the following authentication methods as the primary supported authentication mechanism. The expected release date is the end of February 2013.
Table of Contents
Background
Authentication is the process by which you provide credentials to the server and the server verifies you are whom you claim. At Quicktate, we believe in strong and practical authentication methods. It is of the utmost importance that your transcriptions are secure and not able to be accessed by unprivileged users. That said, as our infrastructure evolves, we are improving the ways by which we perform authentication.
Our XML-RPC and RESTful web services support different means of authentication. This is inherent to the distinct differences of how RESTful and XML-RPC services behave, but also due to legacy concerns. To understand the differences between the two, please read the Authenticating for REST and Authenticating for XML-RPC sections.
Authenticating for REST
Authenticating using the RESTful API is as simple as providing your username and password using HTTP Basic authentication. This is submitted on every request, as our RESTful API is stateless. Security is ensured through the mandatory use of SSL when connecting to the RESTful API.
The HTTP Basic Authentication specification
states that a user must send his username and password as a Base-64 encoded pair with colons inbetween. Therefore,
for a user with username user@quicktate.com and password password, the string to be
Base-64 encoded would be user@quicktate.com:password. This would be sent in the
Authorization header in each request. If the username or password never change, then neither should
the Base-64 encoded representation of them. An example request for the same username and password looks like the following:
GET /api/transcriptionrequest HTTP/1.1
Host: api.quicktate.com
Authorization: Basic dXNlckBxdWlja3RhdGUuY29tOnBhc3N3b3Jk
Accept: application/json
Connection: keep-alive
Content-Type: application/json
Authenticating for XML-RPC
Our XML-RPC API uses a simple username and API key for authenticating every request. These are submitted as parameters in every request. For example, where your payload would normally be the following (pseudo-code):
<array>
<language>1<language>
<metadata>customerId=12345&returnCode=98765<metadata>
<audiourl>https://www.quicktate.com/audio/myaudio.wav<audiourl>
</array>
you would include your username (user) and API key (key) as other parameters
in this payload:
<array>
<language>1<language>
<metadata>customerId=12345&returnCode=98765<metadata>
<audiourl>https://www.quicktate.com/audio/myaudio.wav<audiourl>
<user>user@quicktate.com<user>
<key>38e1d7554e89551538d909d45876b12a<key>
</array>
In the event that you provide an invalid username or API key, you will receive an XML-RPC status code
of 810 with an error message of Login information incorrect.
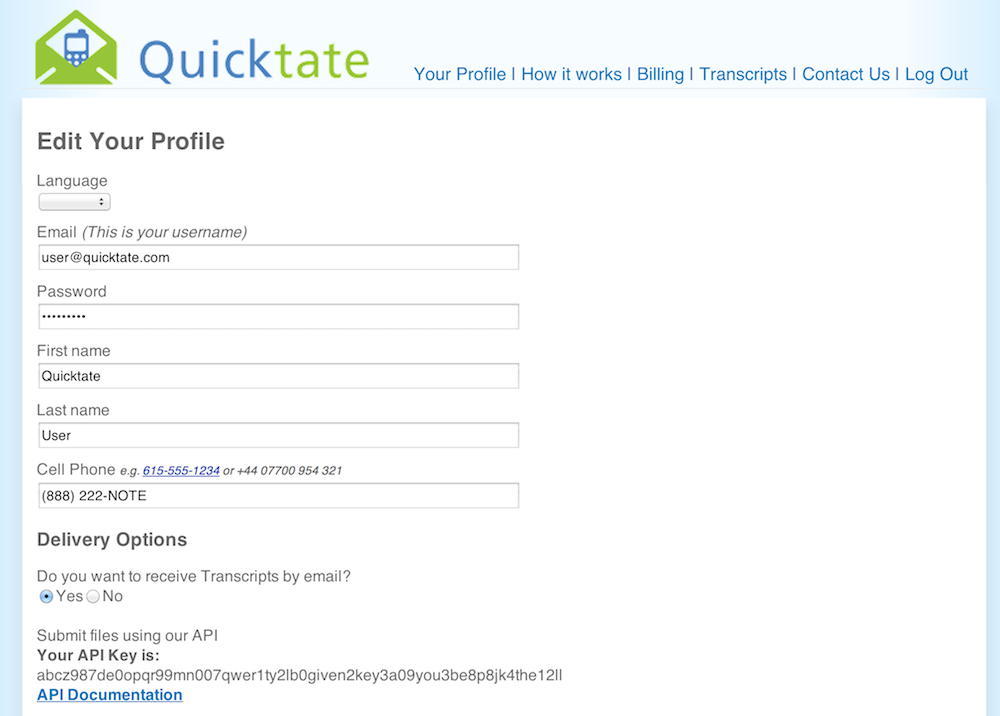
To find your API key, you'll need to login to the Membership Portal.
From there, click the Your Profile link to
see your profile information. You'll find your API key in the section marked Your API Key. See
the following screen shot as a reference.
Although this mechanism has been in-place for several years, due to the deprecation of this API, we will not enhance that security mechanism. If you would prefer a more standards-approved means of authenticating, please use our RESTful API, which supports HTTP Basic authentication, and soon, OAuth.